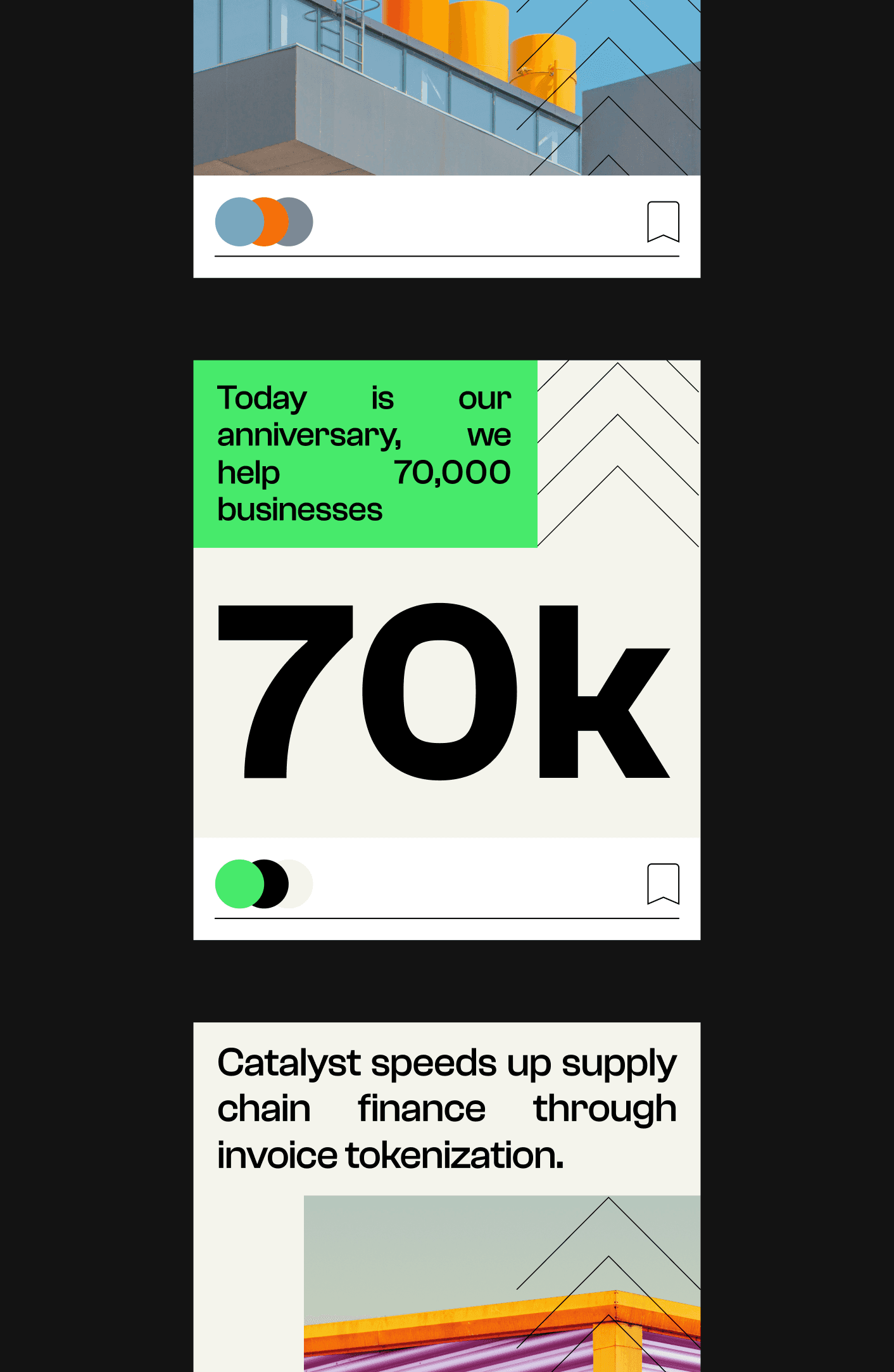
▶ Catalyst is revolutionizing supply chain finance by making it easier
and cheaper for small businesses to access credit.
▶ Catalyst is revolutionizing supply chain finance by making it easier and cheaper for small businesses to access credit.
▶ Catalyst is revolutionizing supply chain finance by making it easier and cheaper for small businesses to access credit.
▶ Catalyst is revolutionizing supply chain finance by making it easier and cheaper for small businesses to access credit.












































































▶ Paytone offers modern financial tools
for the new era of entrepreneurs..

























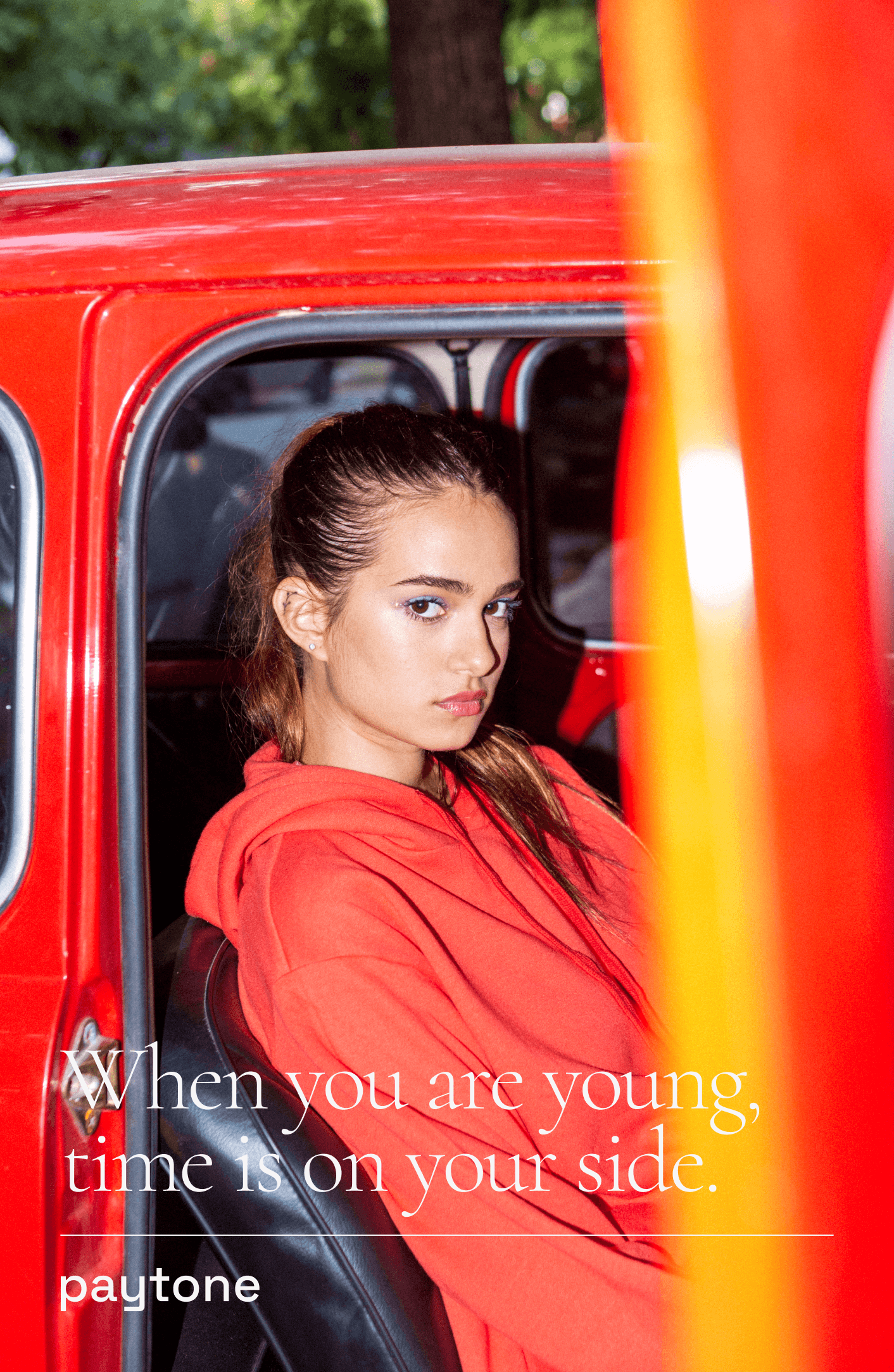
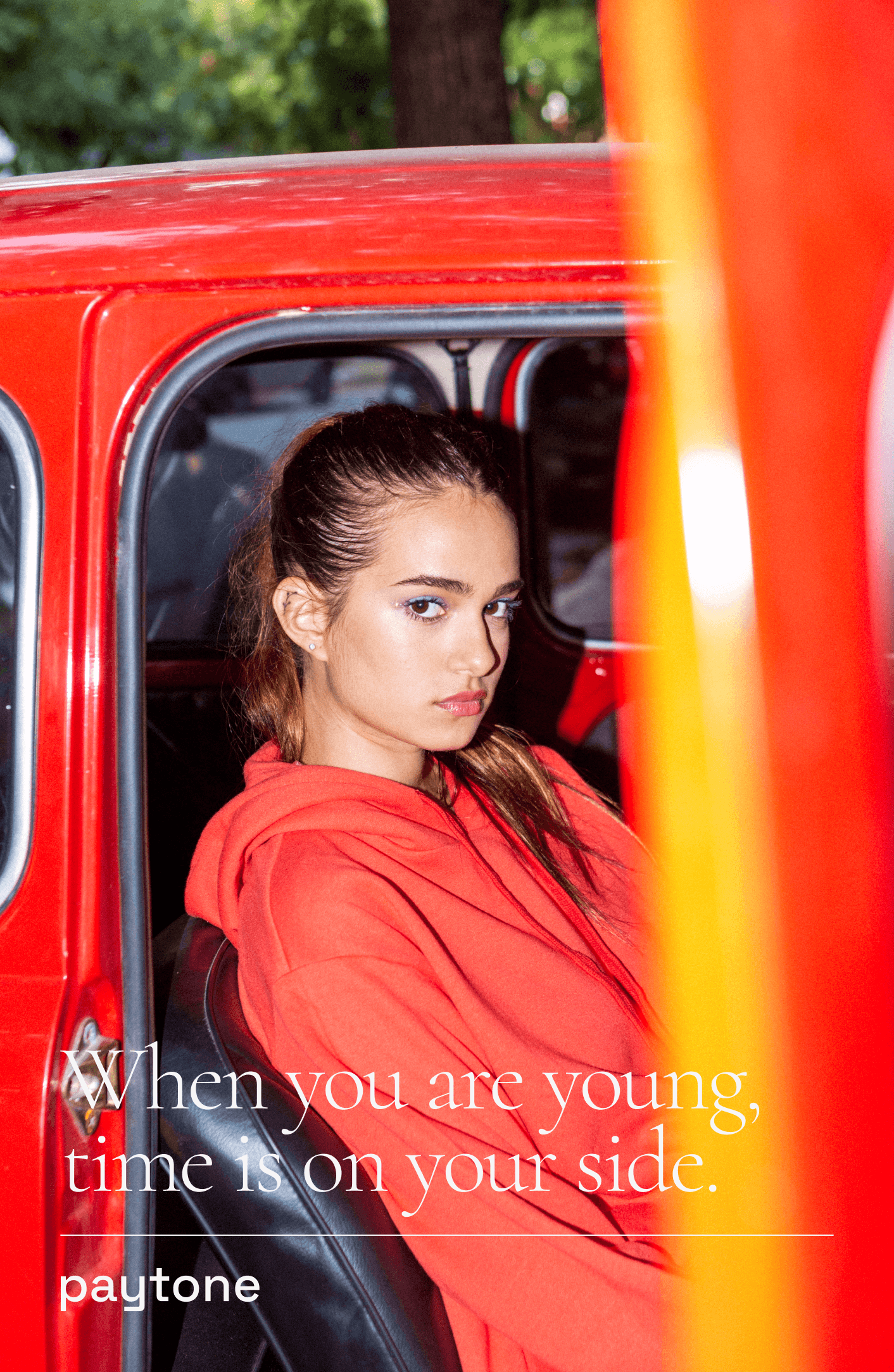
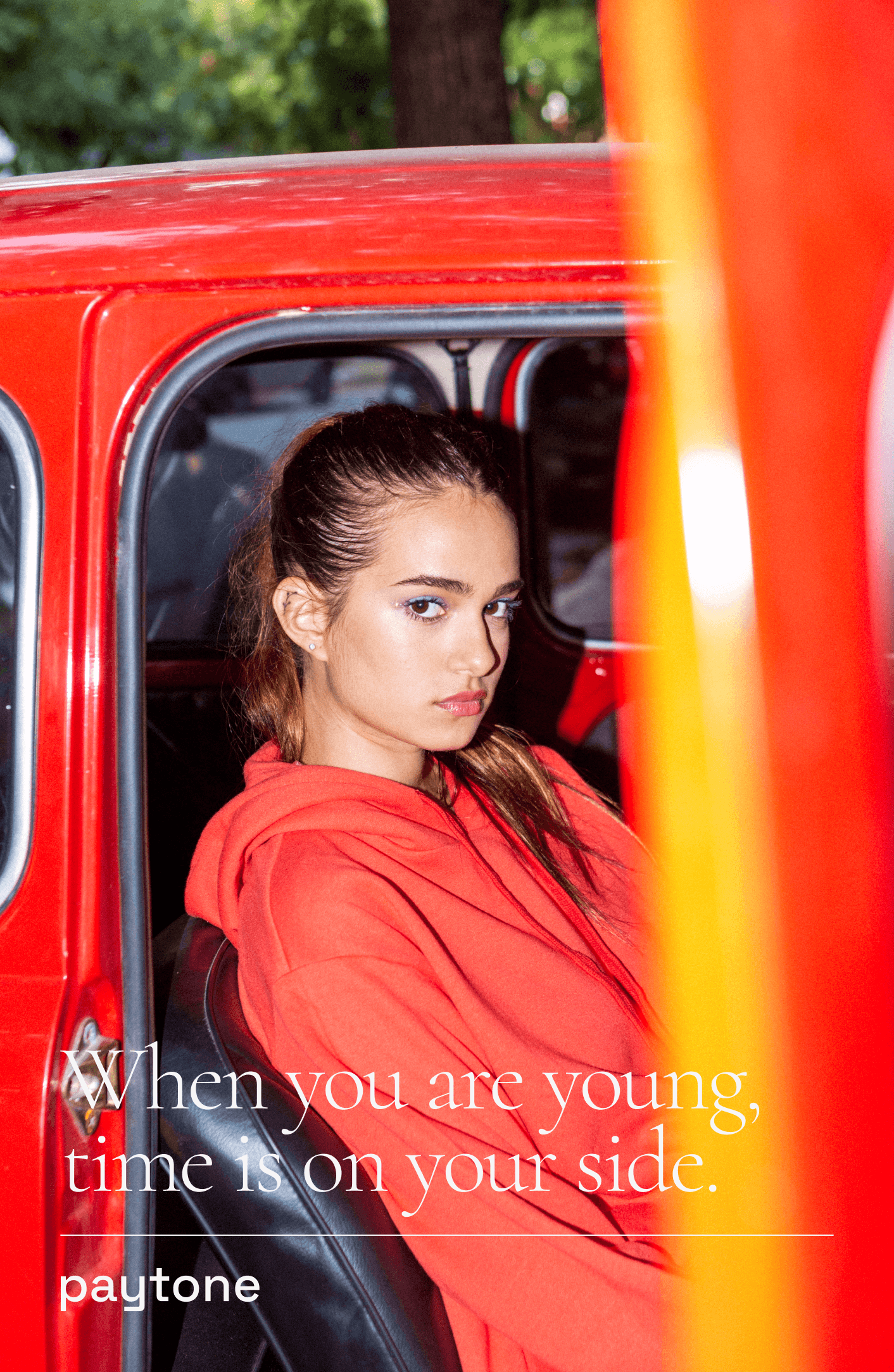
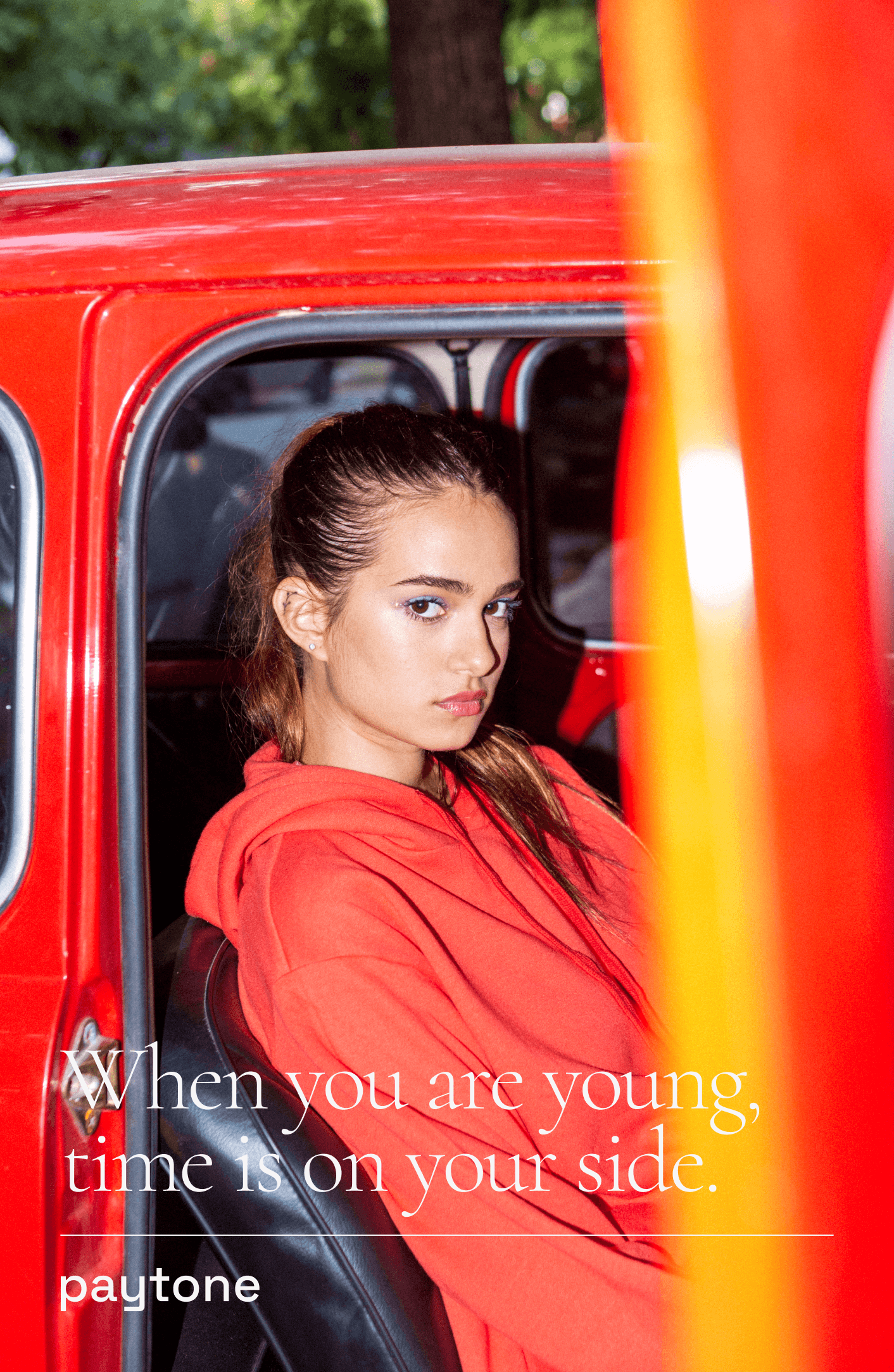
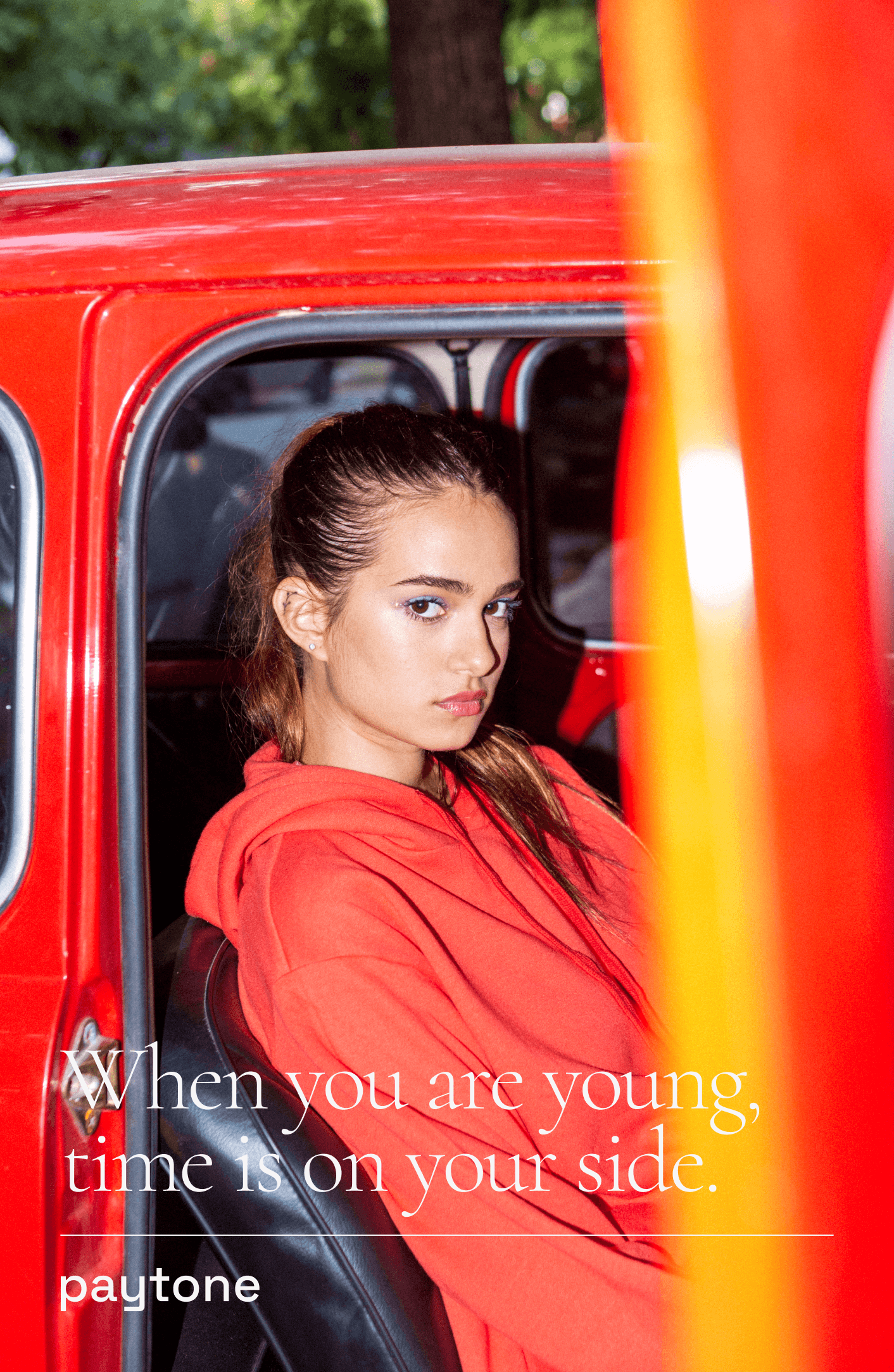
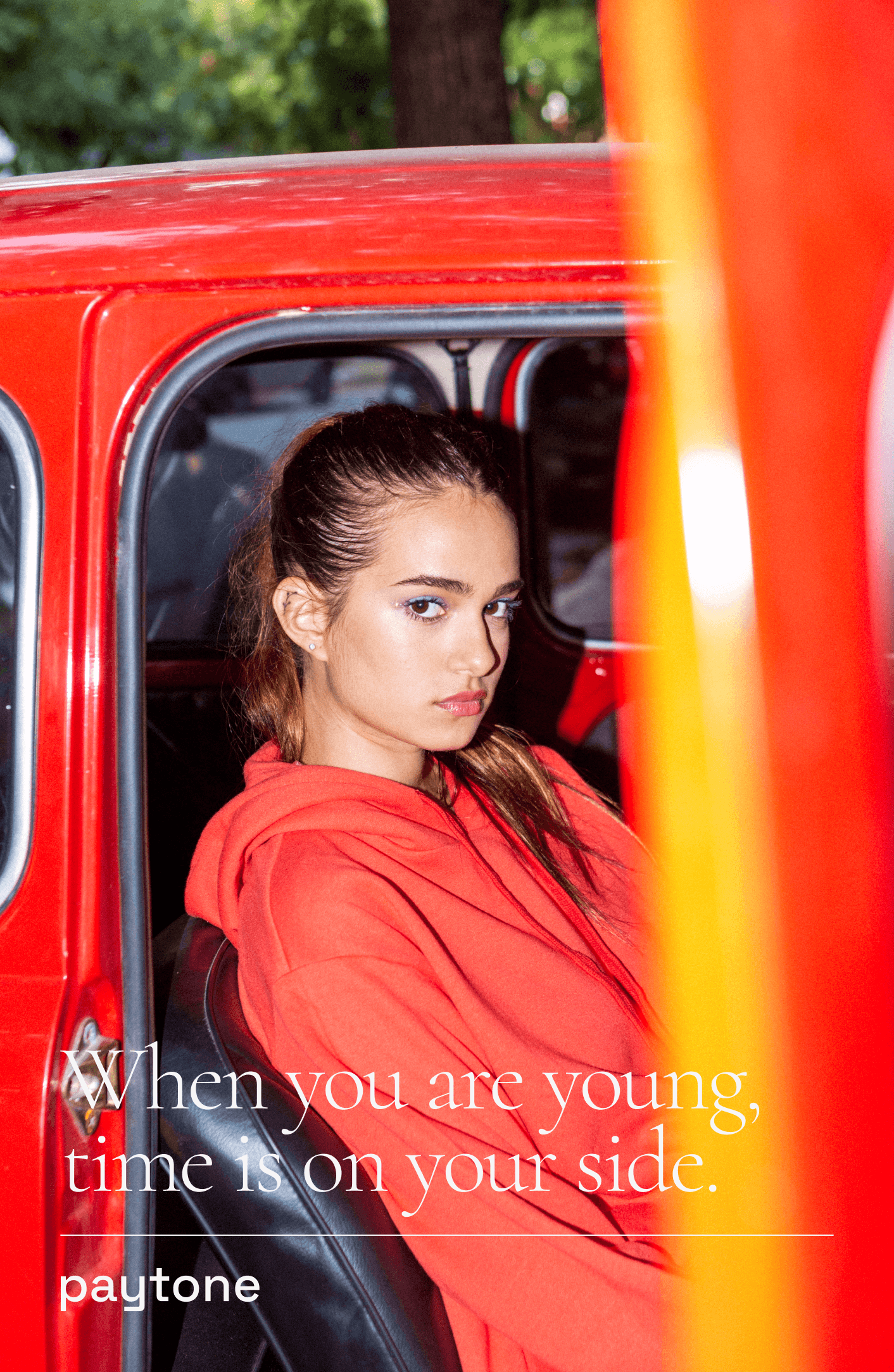
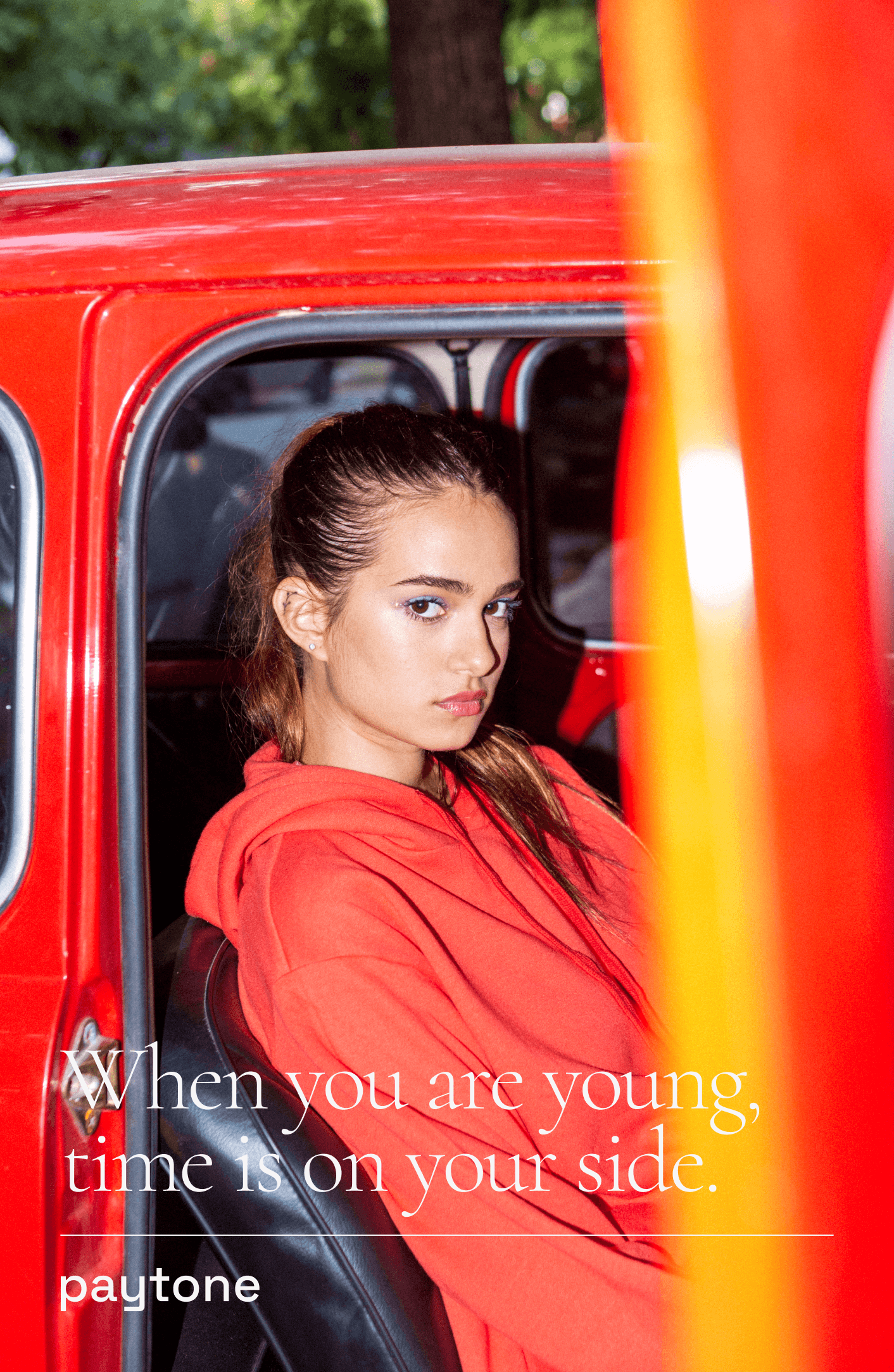














































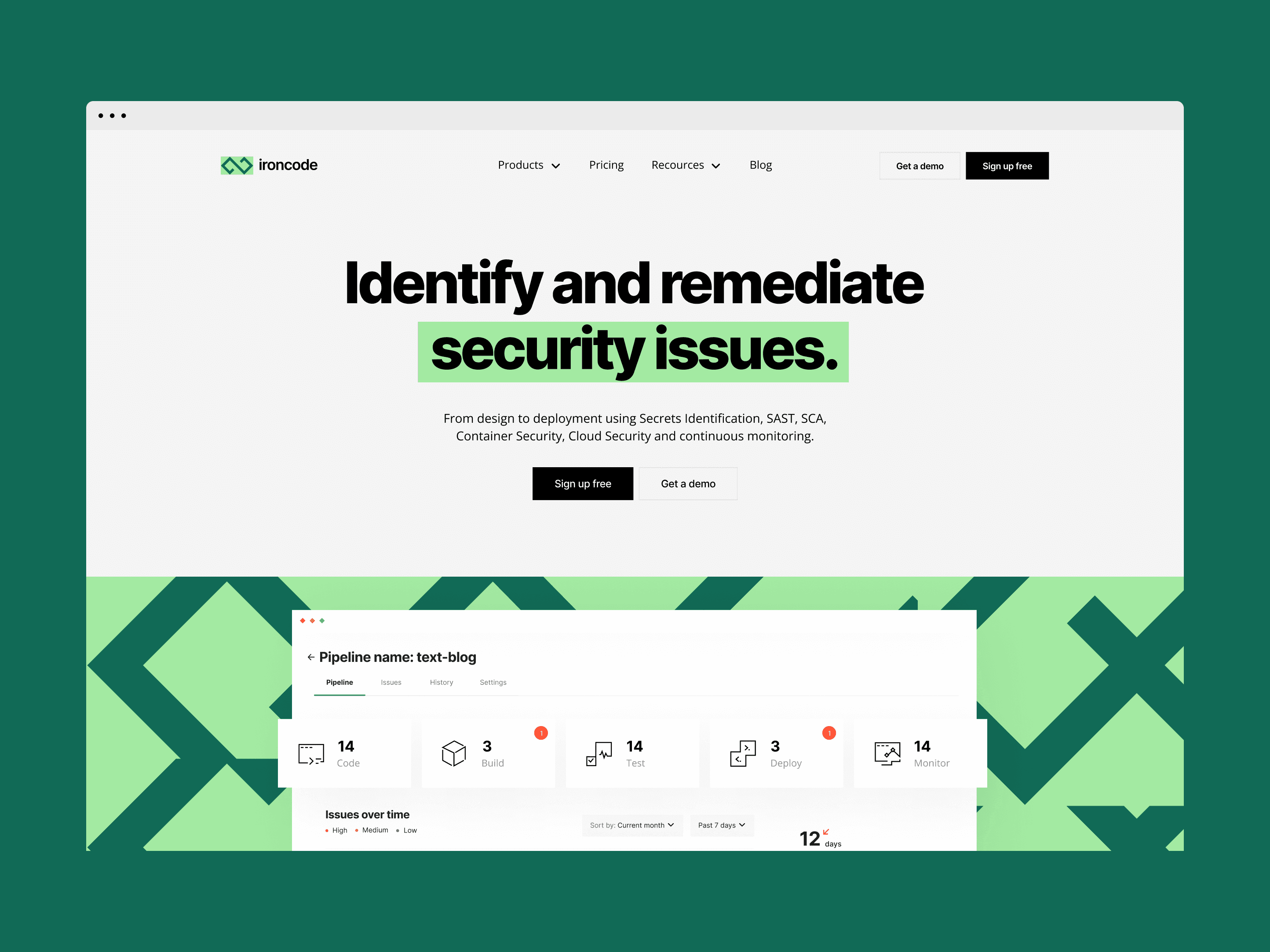
▶ Digital vulnerability. From design to deployment using Secrets Identification, SAST, SCA, Container Security, Cloud Security, and continuous monitoring.
▶ Digital vulnerability. From design to deployment
using Secrets Identification, SAST, SCA, Container Security, Cloud Security, and continuous monitoring.
▶ Digital vulnerability. From design to deployment
using Secrets Identification, SAST, SCA, Container Security, Cloud Security, and continuous monitoring.
▶ Digital vulnerability. From design
to deployment using Secrets Identification, SAST, SCA, Container Security, Cloud Security, and continuous monitoring.





































































































▲ Go up
▲ Go up
My prayers are with my country and its people. Your help would be sincerely appreciated. ◀
My prayers are with my country and its people.
My prayers are with my country and its people.
✺ Hi, I'm Stan Yakusevych — creative director and co-founder of studio. I help SaaS companies & digital products find their perfect look.
✺ Hi, I'm Stan Yakusevych — creative director and co-founder
of studio. I help SaaS companies & digital products find their perfect look.
✺ Hi, I'm Stan Yakusevych — creative director and co-founder of studio. I help SaaS companies
& digital products find their perfect look.
✺ Hi, I'm Stan Yakusevych — creative director and co-founder of studio.
I help SaaS companies & digital products find their perfect look.
My prayers are with my country and its people. Your help would be sincerely appreciated. ◀
My prayers are with my country and its people.
My prayers are with my country and its people.